Online protection is an issue that no one needs to discuss. It’s significant, notwithstanding, on the grounds that the gamble is genuine. While many ventures are as of now doing whatever it may take to safeguard themselves from this quiet danger, there are still a lot of other people who wind up misled by digital assaults.
The development in cybercrime results from a developing number of online hoodlums searching for simple and productive targets. Data fraud represents a threat to everyone nowadays. Entrepreneurs, ordinary workers, and, surprisingly, the VIP at the absolute greatest organizations around are powerless against programmers taking their personalities.
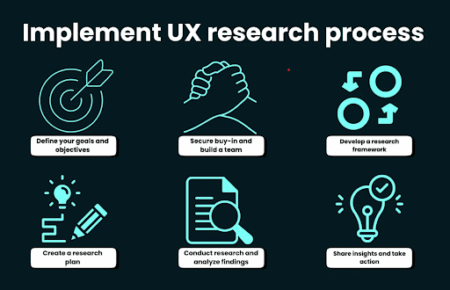
You could ponder, “How might we guard ourselves from something that nobody needs to discuss?” The response: Start being proactive by doing whatever it may take to safeguard yourself, your association, and its individuals. These things will go far to safeguarding your information or classified data:
Effective Ways to Prevent a Cybersecurity Attack

1. Decide Your Risks
The initial move towards safeguarding yourself against cybercrime is to figure out the gamble. Survey the gamble presented by your organization and the dangers that accompany it. What are the dangers? Which are excessively intense to overlook? The mark of this initial step is to give you an idea about what you want to shield yourself from. The subsequent advance is to comprehend what you need to safeguard. It implies knowing the worth of your information.
2. Teaching representatives on not opening dubious messages
Taught representatives are bound to be aware and figure out when a cyberattack is attempting to invade your server. They’re additionally bound to decline a challenge to tap on a connection that could think twice about PCs or the organization. Guarantee you have a data security strategy set up and ensure everybody has perused and grasped it.
An illustration of a decent data security strategy ought to frame what everything your workers may or may not be able to on the web, how they can and can’t safeguard their gadgets, and what they need to do on the off chance that they suspect something is hatching.
3. Use security controls
We’ve all known about antivirus programming, firewalls, and IDS, yet this progression is about something other than introducing these projects on your PCs. You want to introduce an inside and out set of safety controls that safeguards your organization against outer dangers.
It implies a total arrangement of multifaceted verification that can keep programmers out. It additionally incorporates encryption for both back-ups and information very still or on the way. It implies encoding the information very still, scrambling the information on the way, and encoding the reinforcement you keep of the information.
4. Secure your organization
You’ll have to carry out solidifying for your servers and applications. Indeed, these aren’t exactly the same things, yet they work related to one another. The security controls that you use ought to be serious and incorporate various measures, for example, incapacitating superfluous administrations, ending all conventions not pertinent to your business, empowering logging of all associations among servers, and sifting outbound traffic utilizing an intermediary or inbound channels on firewalls.
You’ll likewise need to enact interruption identification frameworks that screen action on the organization for indications of interruption and spring up cautions when something dubious is distinguished. Consider executing a bunch of safety arrangements that oversee OK use in the association.
5. Execute a fix technique
A wide range of sorts of weaknesses can influence your PC and frameworks with regards to arrange security. Some are incorporated into working frameworks or applications, while others come from previous bugs in the codebase.
The best safeguard against digital assaults is to keep steady over fixing. It implies staying aware of all updates, little and enormous, for your equipment and programming. It’s smart to robotize this cycle however much as could be expected with the goal that it doesn’t require up a greater amount of your investment doing different undertakings.
Various sorts of danger entertainers can propagate a cyberattack:
Danger entertainers change in their method of assault and reason, for example, and fear based oppressors are probably going to cause actual harm and digital harm.
One of the most well-known, attainable, and compelling strategies is a Denial-of-Service assault. For this situation, an organization or web server is overflowed with sham solicitations, frequently sent from numerous frameworks. One can serve genuine clients. It impacts the accessibility of the objective, which can be either data you can’t get to some site or you can’t utilize your ATM card.
Another normal assault is the utilization of malware. An infection or trojan assumes command of your framework, encoding the information and keeping you from getting to it.
A third and more intricate type of assault is Social Engineering. The assailant gives a misguided sensation that all is well and good by professing to be a dependable colleague. Also, by getting the client to share individual data by means of email or informal organizations, they can get to a great deal of information. It can prompt wholesale fraud, malware, and the extortion of delicate data.
Security Controls
It’s essential to take note of that security controls are accessible to safeguard an association against these dangers. They include:
Data Security Policy:
An organization strategy illustrating how associations handle and reveal security weaknesses and different dangers. Organization strategies should be current with the most recent industry principles.
Organization arrangements should be current with the most recent industry principles.
Interruption Detection Systems:
Frameworks that screen traffic designs, unapproved admittance to information, and so forth to recognize a digital assault. IDS can go about as a hindrance by it is started to identify assault action before it.
Frameworks that screen traffic designs, unapproved admittance to information, and such to identify a cyberattack are in the works. IDS can go about as a hindrance by it is started to identify assault action before it.
What occurs during a digital assault?
The term cyberattack alludes to any episode wherein an adverse consequence is brought about by PC innovation. It might incorporate deliberate demonstrations, like a bank burglary by an Online Criminal, or unexpected demonstrations, similar to when your client records are penetrated because of an issue in your frameworks.
Fix Management:
It is particularly significant for working frameworks, applications, and program modules.
It stays up with the latest with the most recent security patches, hotfixes, and administration packs. It is particularly significant for working frameworks, applications, and program modules.
Information base Security:
Information base security goes past information stockpiling and safeguards your information while it is being put away, got to, communicated, and discarded. Assuming a break happens, data set security additionally guarantees that the aggressor can’t involve or alter the data as they see fit.
End:
In a world that expects innovation to carry on with work and remain associated, it’s critical to have an arrangement to safeguard yourself from digital dangers. The above advances ought to give you the nuts and bolts to begin with safeguarding your organization. In the event that any of the above advances beyond the realm of possibilities, make sure to request help from experts like MyTek who know how to successfully execute them.