Defensible deletion is a process that prevents the loss of sensitive data after it has been deleted. This is done by identifying the document in question and storing a record of the data associated with it. If the document is deleted, this record is then stored in a log file.
Defensible deletion implementation at high-risk locations
Defensible document deletion implementation at high-risk locations can be a complex task. There are many factors that need to be addressed, including the right technologies and procedures to automate the process. But there are also legal risks involved. Defensible disposition minimizes the risk of damaging litigation and spoliation of evidence.
Implementing an effective defensible disposal program can help your business achieve financial and operational objectives while minimizing risk. Defensible disposition will also improve your organization’s information storage, management, and compliance efforts.
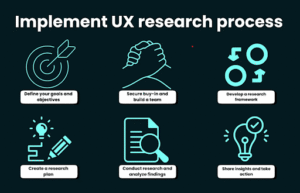
To effectively implement defensible document deletion, you must have a solid plan. It should incorporate a cross-functional committee with representatives from IT, legal, business, and other areas. The committee should also include line-of-business managers and the CIO.
Defensible deletion implementation in a DISCO
Defensible deletion is an information governance policy that can help determine the legal retention requirements for your company. When implemented in an effective manner, it can reduce the risk of damaging litigation, drive cost out of business operations, and improve your financial performance.
A defensible deletion strategy involves systematically eliminating ESI that has no business value. This reduces the risk of losing key documents and improves the speed of retrieval. Defensible deletion is a good way to minimize compliance risks and lower eDiscovery costs.
A successful defensible deletion project requires careful planning. The project should be evaluated regularly. This can identify process failures and areas for improvement.
Defensible deletion implementation in a results table
Defensible deletion, in a nutshell, is a well-defined process of identifying and deleting unneeded records on an ongoing basis. To do this efficiently, you need to understand the legal holds. The best way to do this is to ask your IT and legal department to coordinate their retention policies. For example, it’s possible to develop a records retention policy for targeted data and use the one for all policy to remove unneeded files from the archive.
Defensible deletion might sound like a herculean task, but it’s not. The best way to accomplish this is to break the task into several manageable projects. You can also make this an iterative task by incorporating an automated process into your document retention program.
Lucene fails to kick off any merges
Lucene is an indexing engine that provides text indexing capabilities. It analyzes text and saves the results of its analysis to the index. Its public API provides a relatively simple set of methods for indexing a document.
The public API also hides a more complex set of operations. For example, Lucene uses Directory methods to read and write files. The Directory class hides the details of how it stores documents.
When a Document Deletion, Lucene stores a bit in the per-segment bitset. This bit allows Lucene to track the deletion. It also marks the document as deleted in the index.
When a Document Deletion, the document ID is tied to the shard that contained the deleted document. This causes a non-trivial performance cost. It also consumes disk space in the index.
Logging of data about deleted documents
Fortunately for us, there is a free tool that can do the task in no time at all. Besides being free, the tool is easy to use and has a surprisingly good track record for restoring lost or deleted files. The free tool can also save recovered files to a directory of your choice. It also boasts a nice looking user interface. The tool is also highly configurable, allowing you to choose a user-defined name and password, and even specify the location of the resulting backup. Its a good tool to have in your toolbox, especially if you need to restore a damaged Windows OS.